
July 1, 2019
Cyber Security & Cloud Expo - Levels of Mobile Security
On June 19th and 20st we attended Cyber Security & Cloud Expo in Amsterdam. It was a pleasure to see the interest and curiosity towards freedom of mobile. The idea of relying on handful of options when choosing proper mobile platform for your business, work, mission or personal life is crumbling.
We had great conversations about the information security of companies in areas of gas, power, healthcare and critical communications. Mobile – the weakest link in cybersecurity chain seems to be getting more attention and consideration from security professionals and executives.
It’s known that the era of modern work requires collaboration, communication and information sharing for being productive and innovative regardless of the place and time. The challenge is to do it securely while using highly vulnerable devices - smartphones.
From problems to solutions
We got the chance to introduce our “Multilayered Security Chain”, which secures company’s mobile communications and data sharing based on their needs and threat models from enterprise - to high security - and mission critical needs.
Multilayered Security Chain
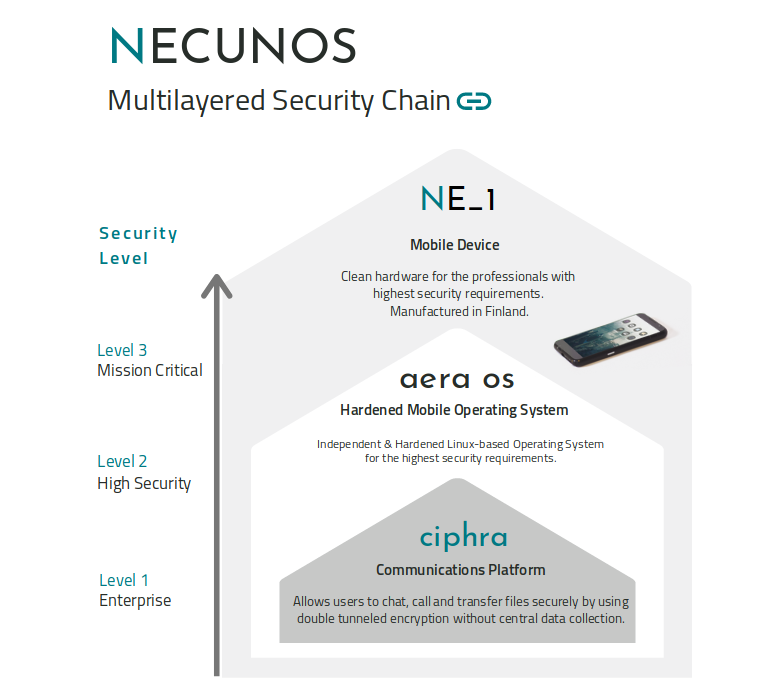
Mobile management solutions and services today can not guarantee the security of the whole device and possibilities for backdoor access are left open. Our mission is to secure each level of the mobile ecosystem, from encrypted messaging to ultra high-level security hardware.
Stay in the loop for more information of each layer in upcoming posts!
You can follow our updates by subscribing to our newsletter from below in the footer and by following us on Twitter.
Contact Us:
contact@necunos.com